Baidu's New Censorship Policies for Leaders' Names After the 18th Party Congress
Prior to November 2012, Baidu's practice was to restrict all queries containing the name of a member of
 |
| Searches on Oct. 27, 2012 for PBSC members' names on Baidu restricted to Sina.com.cn return no results. |
the Politburo Standing Committee of the Communist Party of China ("PBSC") to a strict white list of about a dozen websites controlled by the central government and the Communist Party:
State Run News Outlets
The China Daily (chinadaily.com.cn)
The Economic Daily (www.ce.cn)
The People's Daily (people.com.cn)
The Guang Ming Daily (gmw.cn)
Xinhua (xinhuanet.com)
China News Service (chinanews.com.cn)
State Run Broadcasters
China Radio International (cri.cn)
China Central Television (cctv.com and cntv.com)
Government Agencies
Communist Party Youth League (youth.cn)
Central Government (gov.cn)
State Council Information Office (china.com.cn)
State Council Taiwan Affairs Office(chinataiwan.org)
In early 2012 Baidu also began including its own "Baike" Wikipedia clone in its strict white list - https://plus.google.com/u/0/106378980111121757454/posts/K6wRmyDbJEV.
In the weeks surrounding the 18th Party Congress, which convened from November 8 - 15, Baidu began tweaking its censorship of the names of current and future PBSC members' names, in some cases relaxing its censorship of those names and returning search results from its broad white list, which includes large China-based news and portal websites such as Sina, Sohu, and Tencent. See: http://blog.feichangdao.com/2012/11/as-politburo-standing-committee.html
One month after the conclusion of the 18th Party Congress, Baidu appears to have settled on the following censorship policies for the names of senior government leaders:
- Search results for queries containing only a member's name in Chinese are restricted to the strict white list.
- Searches for member's names on Baidu's Tieba, Zhidao, and Wenku products return no results.
- Search results for queries containing a member's name in Chinese plus a sensitive term are either restricted to the strict white list or censored completely.
- New Search results for queries containing a member's name in Chinese plus a non-sensitive term are restricted to the broad white list.
Some examples:
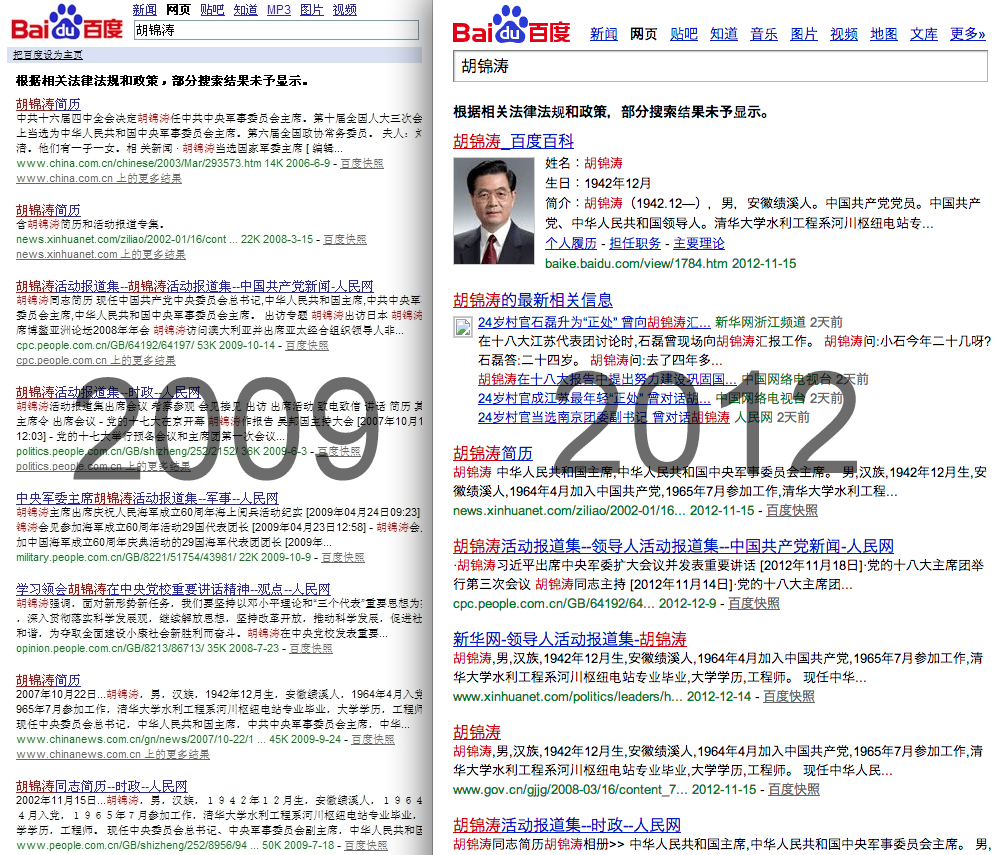
These screenshots show that searches for "Hu Jintao" in 2009 and 2012 only returned results from Baidu's strict white list.
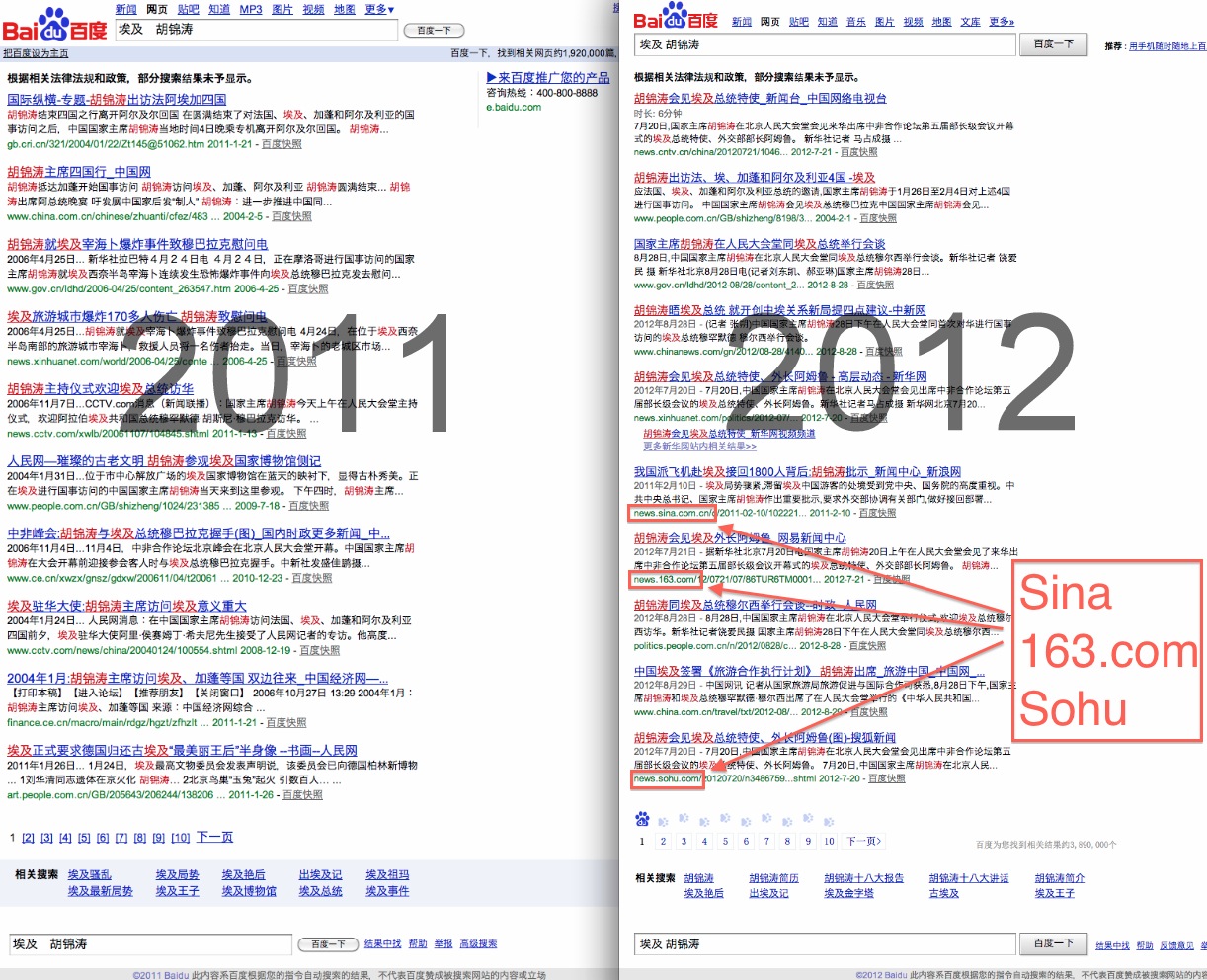
These screenshots show that a search for "Egypt Hu Jintao" in February 2011 only returned results from Baidu's strict white list. The same search in December 2012 returned results from Baidu's broad white list.
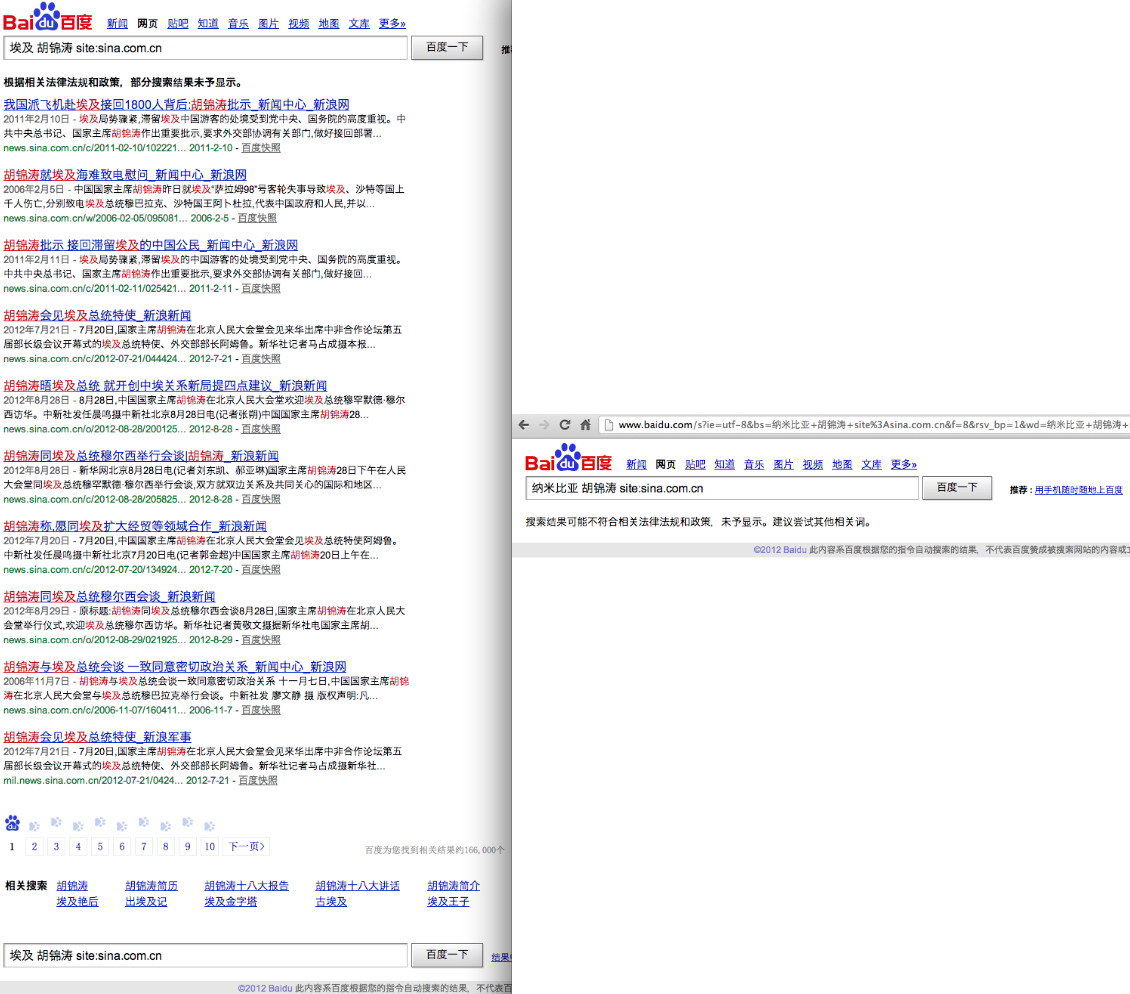
These screenshots, taken in December 2012, show that a search for "Egypt Hu Jintao site:sina.com.cn" returns tens of thousands of search results, while a search for "Namibia Hu Jintao site:sina.com.cn" returns no results, only a censorship notice.
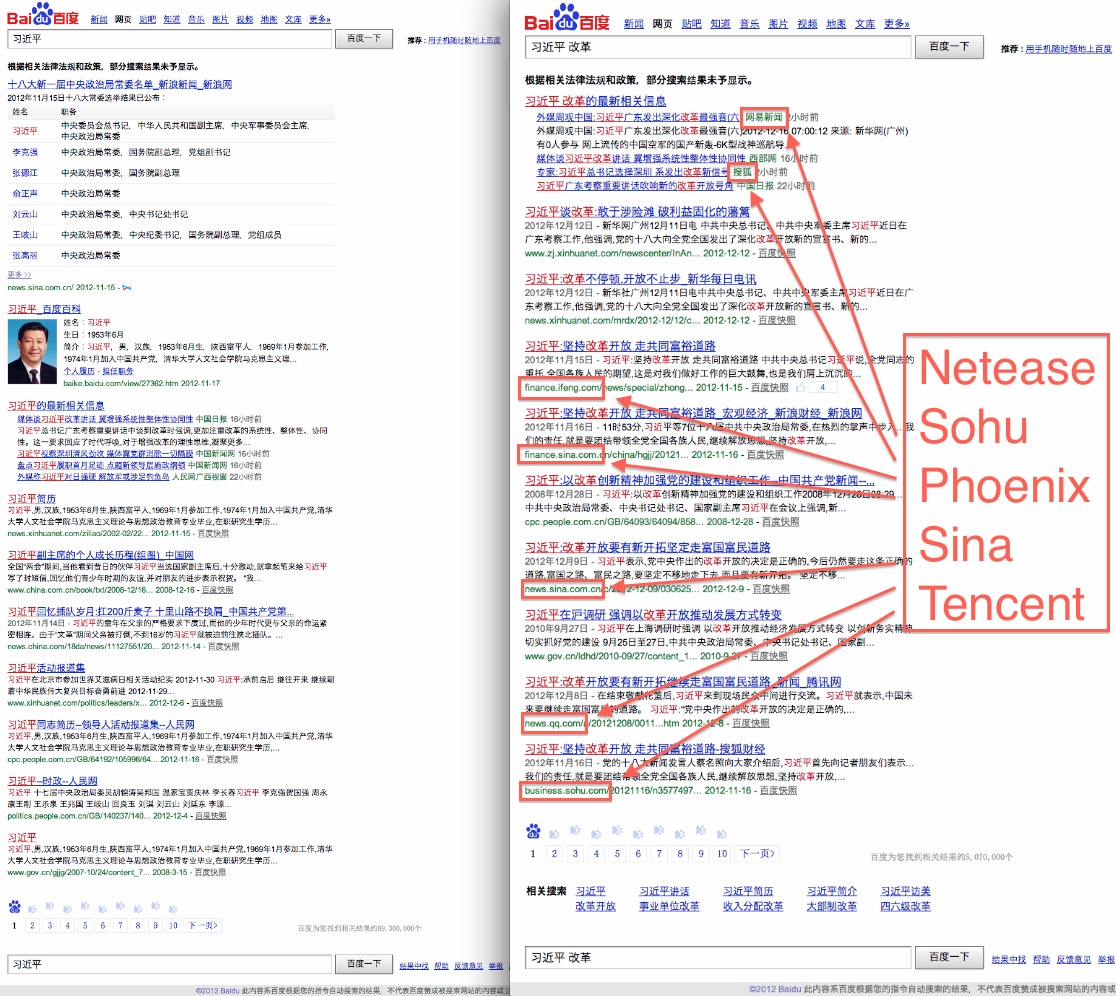
These screenshots, also taken in December 2012, show that a search for "Xi Jinping" only returns results from Baidu's strict white list, but a search for "Xi Jinping Reform" returns results from Baidu's broad white list.
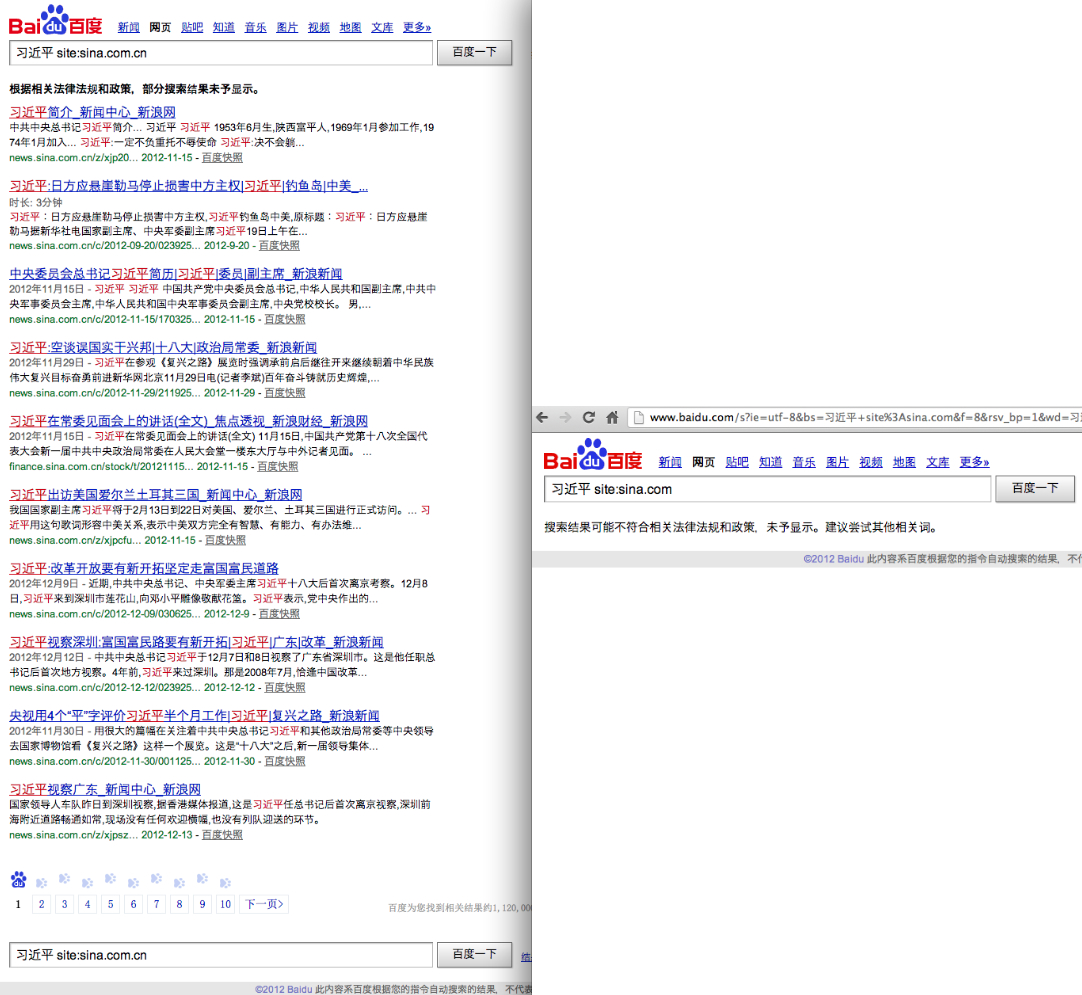
But these screenshots show that, while Baidu returned over a million results for a search for "Xi Jinping" restricted to the China-based Sina.com.cn, the same search on the Hong Kong-based Sina.com returned no results, just a censorship notice.
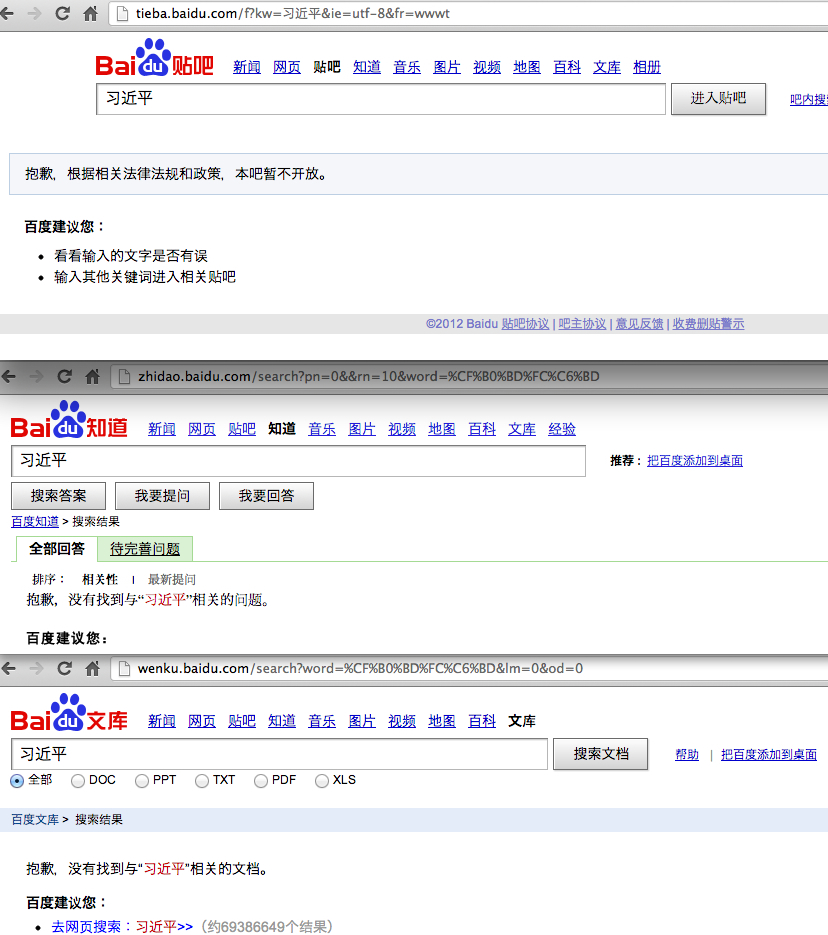
Finally, these screenshots, also taken in December 2012, show that a search for "Xi Jinping" on Baidu's Tieba, Zhidao, and Wenku products still returns no results.
From http://blog.feichangdao.com/2012/12/baidus-new-censorship-policies-for.html