Gmail is getting faster but still not as fast as dial-up
Many in China have complained that Gmail is so slow that it is almost impossible to use (see our original story from March 2011 - Gmail now 45 times slower than QQ). We have continued to gather data on the Gmail situaiton in light of Google's continued operation in China. With more data we can now show how the situation has developed since March. The results are clear in this chart:
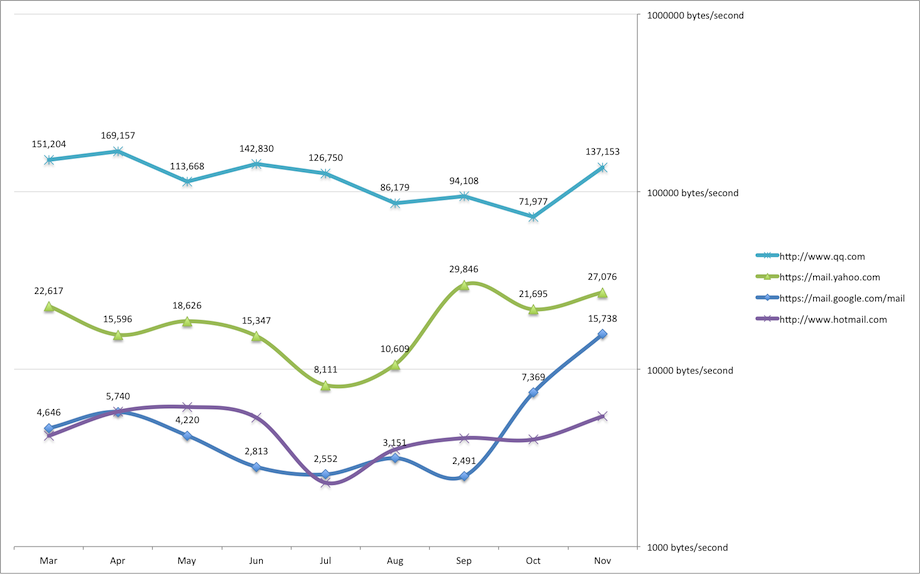
All foreign webmail providers are considerably slower than domestic competitors (QQ is included for comparison). Out of Gmail, Hotmail and Yahoo, a distressed Yahoo, whose local partner in China is Alibaba, is consistently the fastest free foreign email provider. Hotmail has at times challenged Gmail to a race to the bottom. Using the same comparison as in March, Gmail is now only 9 times slower than QQ and has seen a considerable improvement in speed since September.
One way to put the speed of Gmail into perspective is to compare today's access speed with old dial-up modems, for those that remember. In the 1990s, they provided speeds up to 56 kbps, or roughly 7000 bytes per second. That is considerably faster than the average speed of either Gmail or Hotmail, when accessed from within China in 2011.
Apart from speed, the main problem with Gmail in China is instability. Rather than blocking the service outright, it seems that the authorities have chosen to impose occasional, random outages. Looking back over the year (from March onwards), we can see the following:
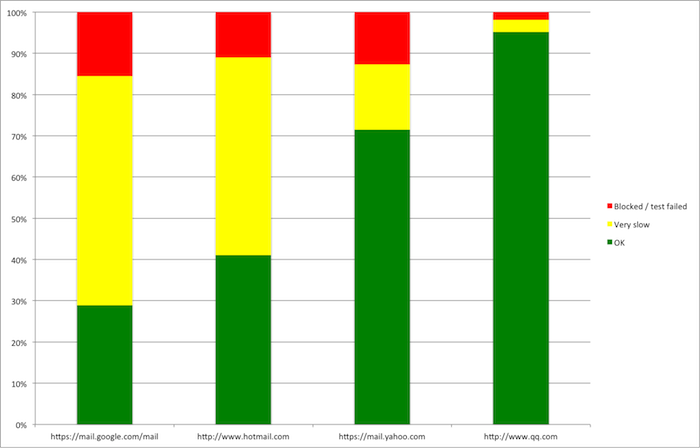
Gmail has had an acceptable download speed less than 30% of the times we've tested it. Most of the time, it's very slow (meaning less than 5000 bytes/second). Our data suggests that all foreign webmail services are temporarily blocked from time to time. Again, Yahoo performs better than either Gmail or Hotmail.
Data from QQ is included for comparison reasons. As QQ is hosted in China, it would not be blocked by the Great Firewall. While the data may indicate that QQ has been blocked at times, this is most likely due to problems with the test location or data noise. Please allow a margin of error of plus or minus 3% on all data which appears on this web site.
The data is based on 776 individual tests from March onwards. You can check the latest data for webmail services here.
