Look Ma! I can see through the great firewall!
Today we have decided to take the battle against online censorship in China to a new level.
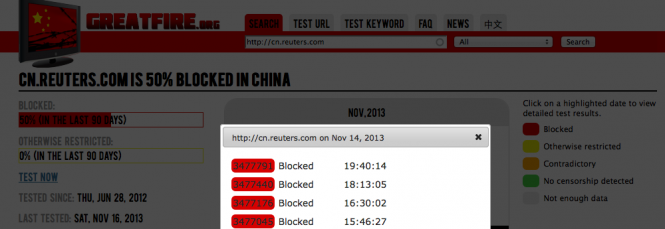
On Friday, November 15, we broke the news that the websites for Reuters Chinese and Chinese Wall Street Journal were both blocked in China. Tests on our servers confirmed those blocks.
It appears that the block is related to the New York Times story published on November 14 concerning the relationship between JPMorgan Chase and Lily Chang (also known as Wen Ruchun), the daughter of former Chinese prime minister Wen Jiabao.
Reuters Chinese published news about the story on November 14, which is probably the reason the site was blocked.
In response to this block, we have just launched a mirror site for Reuters China, which is accessible here:
https://s3.amazonaws.com/cn.reuters/index.html
This website is accessible from within China without the use of any circumvention tools.
PLEASE NOTE: We have created this mirror website without seeking the approval of Reuters ahead of time. This mirror website was created without Reuters’ knowledge. If Reuters ask us to remove this website, we will do so immediately.
We have already used this method or mirroring for our own blocked website, FreeWeibo.com:
https://s3.amazonaws.com/freeweibo/index.html
FreeWeibo shows weibo content that has been blocked by Sina and the Chinese government. Our official domain has long been blocked in China. Despite the block, we still have more than 15,000 visitors each day, a majority of which are using Internet circumvention software to get around the great firewall (GFW) of China.
We want to provide internet users in China with unrestricted information access. Internet circumvention software is for the most part stable in China but one needs to have some technical savvy for configuration.
With our new mirror sites, the GFW cannot block FreeWeibo.com any longer without causing significant collateral damage which would also cause significant economic fallout in China.
Our mirror sites are unique because rather than using our own domains, we use a subpath of Amazon and Google’s domains which support HTTPS access. This means that GFW cannot block our mirror websites without blocking the domain of Amazon or Google entirely, namely “s3.amazonaws.com” and “commondatastorage.googleapis.com”.
GFW might indeed go ahead and block these domains but it would risk considerable negative backlash and may cause problems economically for organizations within China that rely on these services. In January 2013, China blocked Github supposedly for having sensitive content. But the block created a fierce outcry in the Chinese developer community. Subsequently, the authorities backed down and stopped blocking the domain.
Our mirror site is not perfect! There are a few minor bugs in what we have created. However, we wanted to quickly put this together so that we could fire a shot across the bow of the Chinese censorship mothership.
The reason why we chose to mirror the Reuters Chinese web site was to show the authorities and Chinese internet users that there are holes in the great firewall. To plug this hole, the Chinese authorities have two options. They can block the Amazon and Google domains, thereby bringing down thousands of websites in China that rely on these web services. This will bring the issue of online censorship to a very large group of people in China. The other option is to force Amazon or Google to remove our sites willingly. We have previously reported that Apple willingly remove OpenDoor, an Internet circumvention tool, from the China App store and this week there were reports about self-censorship at Bloomberg. We hope Amazon or Google will not practice the same kind of self-censorship.
There is a third option. Mr. Xi Jinping, we hope you are listening. Just let this episode slide. Pretend it did not happen. Do nothing to stop this. Or, better yet, lift the block on these two websites and the hundreds of others. Do it in one swift movement. You will catch everybody off guard. And you will create your own lasting legacy as a true reformer.
We have participated in OpenITP’s report “Collateral Freedom: A Snapshot of Chinese Users Circumventing Censorship” and we fully agree with their conclusion:
The essence of the Internet freedom debate in China is segmentation, not blocking. When crucial business activity is inseparable from Internet freedom, the prospects for Internet freedom improve.
...
But, we would argue, a healthier response might move in the opposite direction, toward even greater integration between Internet freedom and business. Rather than working with particular online platforms, which may be individually vulnerable to censorship, the best long term answer might be to move anti-censorship deeper into the network infrastructure, incorporating it within the systems that large network operators use to exchange their traffic. Ideally, we might aim for a situation in which secure web access generally (rather than access to any particular platform) is inseparable from Internet freedom.